All modern Linux operating systems use the /etc/shadow file to store user passwords in an encrypted hashed format. Only root users or commands with suid bit can access the /etc/shadow file. All other user information, such as user names, home directory, and default shell, is stored in the /etc/passwd file. Let us learn more about the passwords of the users located in the Linux operating system and related commands.
As stated earlier, the /etc/passwd is the password file that stores each user account without password. However, the passwords located in Linux /etc/shadow file. It stores the password hash information for the user account and optional password ageing information. Finally, the /etc/group file is a text file that defines the groups on the system. Each user has one entry per line in those two files.
| Tutorial details | |
|---|---|
| Difficulty level | Easy |
| Root privileges | Yes |
| Requirements | Linux terminal |
| Category | User Management |
| OS compatibility | Alma • Alpine • Arch • CentOS • Debian • Fedora • Linux • Mint • openSUSE • Pop!_OS • RHEL • Rocky • Stream • SUSE • Ubuntu • WSL |
| Est. reading time | 5 minutes |
Where are the passwords of the users located in Linux?

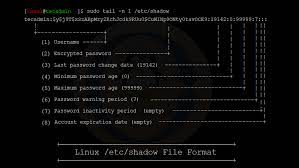
The encrypted passwords and other information such as password expiry information (the password aging information) are stored in /etc/shadow file. All fields are separated by a colon (:) symbol. It contains one entry per line for each user listed in /etc/passwd file. Generally, shadow file entry looks as follows:
The order is as follows:
- Username : It is your login name.
- Password : It is your encrypted password hash. The password should be minimum 8-12 characters long including special characters, digits, lower case alphabetic and more. Usually password format is set to $id$salt$hashed, The $id is the algorithm used On GNU/Linux as follows:
- $1$ is MD5
- $2a$ is Blowfish
- $2y$ is Blowfish
- $5$ is SHA-256
- $6$ is SHA-512
- Last password change (lastchanged) : Days since Jan 1, 1970 that password was last changed
- Minimum : The minimum number of days required between password changes i.e. the number of days left before the user is allowed to change his/her password
- Maximum : The maximum number of days the password is valid (after that user is forced to change his/her password)
- Warn : The number of days before password is to expire that user is warned that his/her password must be changed
- Inactive : The number of days after password expires that account is disabled
- Expire : days since Jan 1, 1970 that account is disabled i.e. an absolute date specifying when the login may no longer be used.
A password hash is nothing but a string that verifies the integrity of your password during login against the stored hash so that your actual password never has to be held in /etc/shadow file. It is a security feature.
How to view the contents of the /etc/shadow file
The normal user cannot access the /etc/shadow file directly. For example, try out the following cat command or more/less/bat command as follows:
$ cat /etc/shadow
Here is what you will see:
cat: /etc/shadow: Permission denied
You can only access the /etc/shadow file via few commands such as the passwd command. Login as root user and execute cat command on /etc/shadow file:
$ su -
Provide root user password when prompted:
Password:
Now, try to display the file:
# cat /etc/shadow
Sample outputs:
root: $1$s83Ugoff$EDT83WAAFpCQHWDp07E9Ux:0:99999:7::: daemon:*:13031:0:99999:7::: bin:*:13031:0:99999:7::: .... ......
Here is how my encrypted password hash looks on Linux:
vivek:$6$LONG_STRING_HASH_HERE1:18770:0:99999:7:::
We can use the chage command to get account aging information in easy to understand format:
$ chage -l vivek
And now I see:
Last password change : May 23, 2021 Password expires : never Password inactive : never Account expires : never Minimum number of days between password change : 0 Maximum number of days between password change : 99999 Number of days of warning before password expires : 7
Each each entry in the /etc/shadow (or outputs from the chage command) is divided into following fields:
- vivek – Login name
- $6$LONG_STRING_HASH_HERE1 – Encrypted password hash
- never – Days since Jan 1, 1970 that password was last changed
- 99999 – Days before password may be changed
- never – Days after which password must be changed
- 7 – Days before password is to expire that user is warned
- never – Days after password expires that account is disabled
- 0 – Days since Jan 1, 1970 that account is disabled
Where and how are passwords stored on Linux
Of course, you can use the sudo command as follows. For example, if you are a Linux system administrator or part of an admin group, then:
$ sudo cat /etc/shadow
Or grep command along with the sudo:
$ sudo cat /etc/shadow | grep vivek
OR avoid useless use of the cat command:
$ sudo grep vivek /etc/shadow
Please note that FreeBSD uses /etc/master.shadow file.
Say hello to getent command
To get entries from Name Service Switch libraries use the getent command. The syntax is:
$ getent database key
$ getent [option] database key
Where database can be:
- passwd – Read user account info.
- shadow – Read user password info.
- group – Read group info.
- key – Can be a user name/group name.
Examples
Try these examples:
$ getent passwd
$ getent passwd vivek
$ getent group
$ getent group vivek
$ sudo getent shadow
$ sudo getent shadow vivek
Conclusion
Now you know where are the passwords of the users located in Linux. I suggest that you read the following man pages using the man command or help command (you can read them online on Debian or Ubuntu manual page section too):
$ man getent
$ man 5 shadow
$ man 5 passwd